A new strain of malware has been targeting mobile banking apps and crypto wallets on Android phones.
The fraud prevention firm ThreatFabric says the new malware, which it named “Crocodilus,” is a trojan that utilizes remote control, black screen overlays and advanced data harvesting.
Crocodilus uses dropper malware, which is designed to bypass Android restrictions, to access victims’ systems. After it’s installed, the trojan requests the victim to enable Accessibility Service.
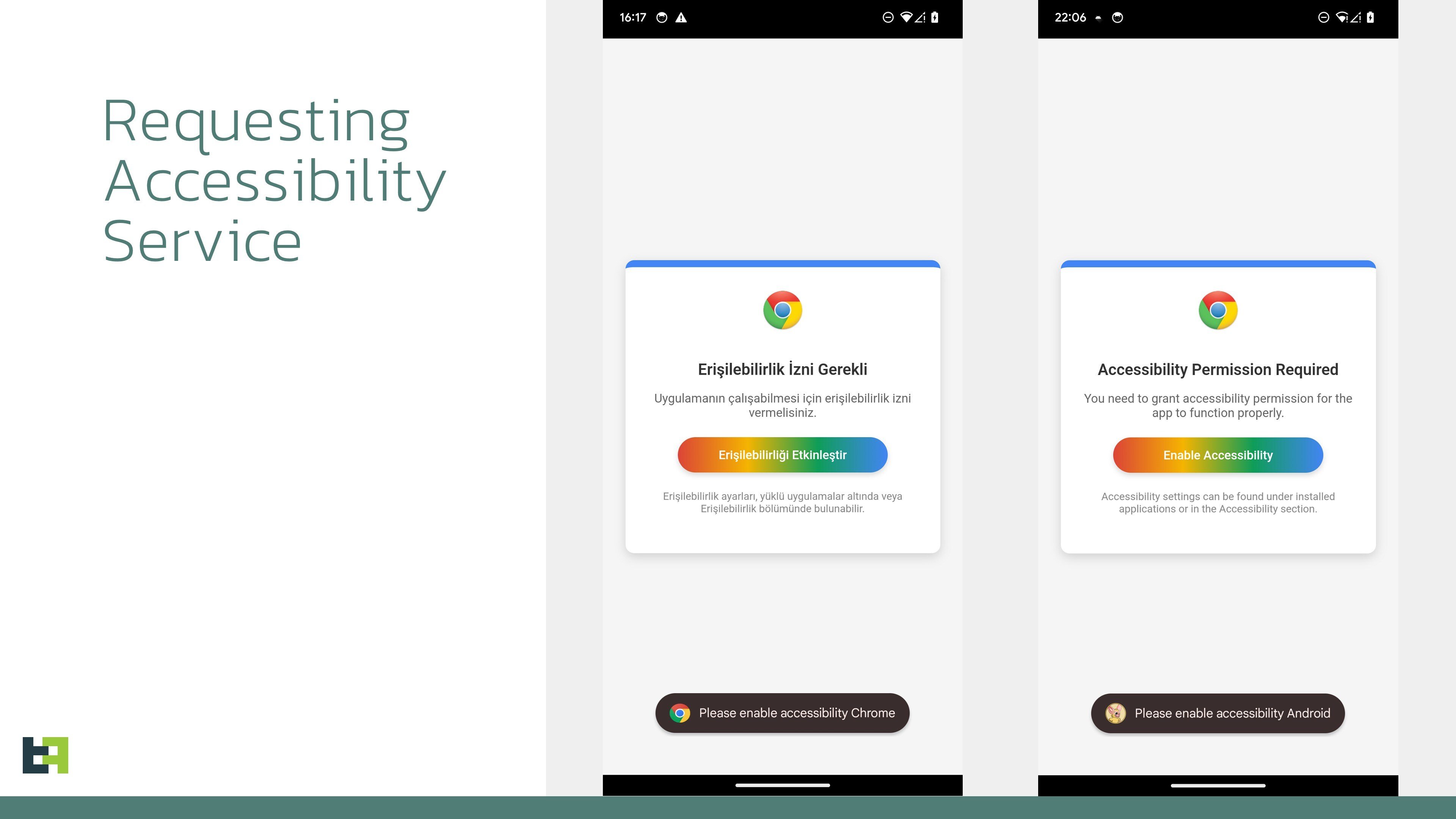
The malware then uses overlays, which run deceptive applications on top of victims’ actual apps to trick them into divulging their credentials.
Explains ThreatFabric,
“Initial campaigns observed by our Mobile Threat Intelligence team show targets primarily in Spain and Turkey, along with several cryptocurrency wallets. We expect this scope to broaden globally as the malware evolves.
Another data theft feature of Crocodilus is a keylogger. However, it is more accurate to call it an Accessibility Logger – the malware monitors all Accessibility events and captures all the elements displayed on the screen. In this way, it effectively logs all text changes performed by a victim, making it a keylogger, but the capabilities go beyond just keylogging.”
The fraud prevention firm notes that when victims submit their PINs or passwords to Crocodilus’s crypto wallet overlays, the malware will display a message saying,
“Back up your wallet key in the settings within 12 hours. Otherwise, the app will be reset, and you may lose access to your wallet.”
The message is designed to convince victims to navigate to their seed phrases, which the malware then steals with its accessibility logger.
Follow us on X, Facebook and TelegramDon't Miss a Beat – Subscribe to get email alerts delivered directly to your inbox
Check Price Action
Surf The Daily Hodl Mix
Generated Image: Midjourney















No comments yet