Security firm Kaspersky has warned about new malware targeting crypto users through the software-hosting website SourceForge. In a recent publication, the firm said the software project on the website, Office Package, contains an address-poisoning malware targeting crypto users.
According to the report, the Office package software is a legitimate project containing Microsoft Office add-ins. However, a closer investigation reveals more about the package, as it contains download links that lead to a different URL.
It said:
“The project under investigation has been assigned the domain officepackage.sourceforge[.]io, but the page displayed when you go to that domain looks nothing like officepackage on sourceforge.net.”
Interestingly, the malware download process is quite complex, with users going through three URLs before they can download the file. The complex process appears to be part of the scheme to lure users into believing they are downloading a genuine application.
Kaspersky security experts noted the final installation file is installer.msi, a 700-megabyte file that bad actors inflated size to make it look like an authentic software installer. After stripping away the junk bytes, the real size is seven megabytes.
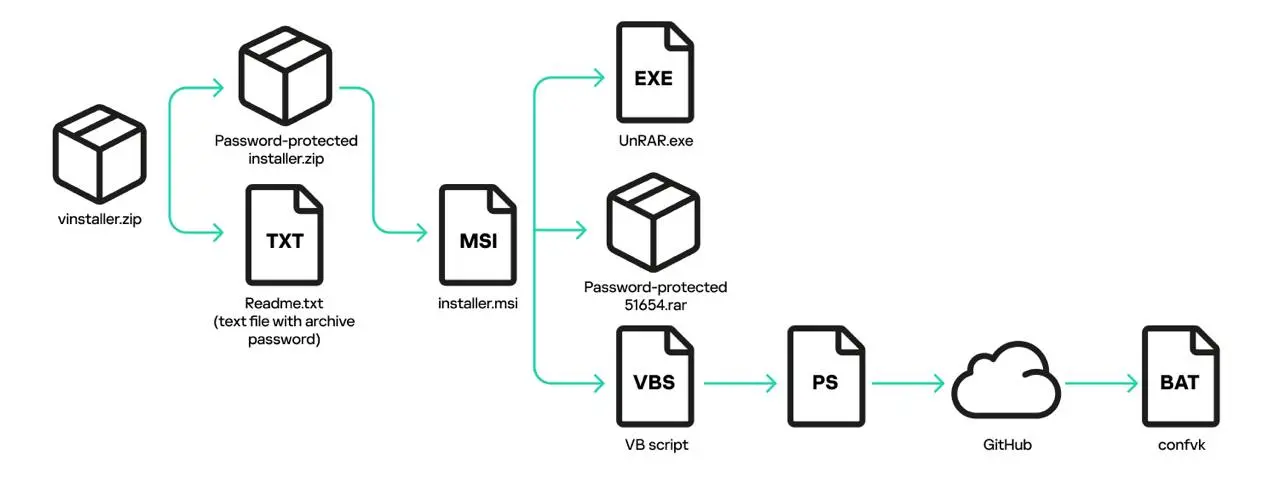
By running the installer, users unwittingly install two malicious applications into their devices, a miner and a ClipBanker. The ClipBanker allows address poisoning by replacing crypto addresses copied onto the clipboard with those of the attacker, leading users to send funds to the wrong addresses.
The security experts wrote:
“The key malicious actions in this campaign boil down to running two AutoIt scripts. Icon.dll restarts the AutoIt interpreter and injects a miner into it, while Kape.dll does the same but injects ClipBanker.”
Meanwhile, they also noted that the attack focused mostly on Russian targets. Signs of this include the Russian interface for the officepackage.sourceforge[.]io site and the fact that 90% of the 4,604 users encountered the malware between January and late March are Russian.
Address poisoning scams increasing
The Kaspersky report corresponds with the recent rise in address poisoning attacks on crypto users, as reported by several blockchain security firms. According to data from Scam Sniffer, the third-biggest phishing incident in March was due to address poisoning.
Cyvers also reported that address poisoning scams caused a loss of more than $1.2 million within the first three weeks of March, adding to the $1.8 million in February. The firm said its AI threat detection system identified an increase in address poisoning attacks.
While most address poisoning attacks result from attackers manually sending small transactions to the victims with addresses similar to the ones they frequently use, the use of sophisticated malware that allows attackers to change addresses from the clipboard shows how bad actors continue to evolve.
Security experts believe the number one solution to this problem is for users to avoid downloading software from untrusted sources. They noted that bad actors usually exploit unofficial software websites to distribute malicious applications, and people using such websites must be aware of that risk.
However, they noted that this malware presents an even bigger problem as provides an inventive way for attackers to gain access to infected systems. Thus, there is a possibility that the creators can decide to use it for more than targeting crypto users and start selling it to more dangerous bad actors.
Cryptopolitan Academy: Want to grow your money in 2025? Learn how to do it with DeFi in our upcoming webclass. Save Your Spot















No comments yet